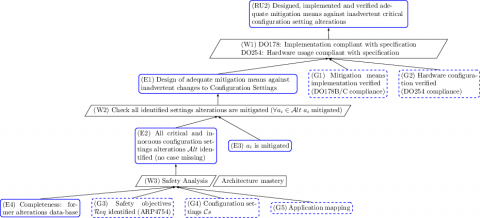
The applicant has planned, developed, documented, and verified a means that ensures that in the event of any of the Critical Configuration Settings of the multi-core processor being inadvertently altered, an appropriate means of mitigation is specified.
Again we observe as the root the CAST-32A objective. To ensure the fault-tolerance of the multi-core in presence of alteration events, there is probably some additional software. This means that again there is some DO178-related activities. Moving to the design itself (E1), it results from the checking that all possible alterations are properly mitigated (W2). The strategy relies on the fact that all critical alterations have been identified (E2) and mitigation means have been developed in front of each potential alteration (E3). (E2) results from a safety analysis that identifies failures and their effects (W3). This analysis applies on the configuration settings (G3), the failures that may encounter each configuration (from expert knowledge and former data base (E4)) and the boundaries expected by the system (G2).