Objective:
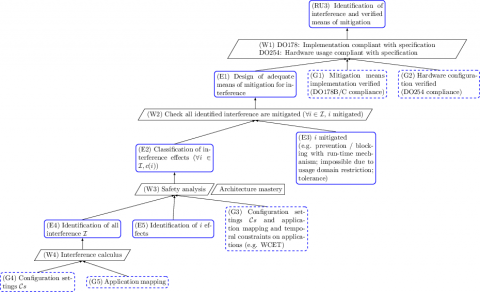
The applicant has identified the interference channels that could permit interference to affect the software applications hosted on the multi-core processor cores, and has verified the applicant’s chosen means of mitigation of the interference.
Again we observe as the root the CAST-32A objective and there may be some software developed for managing interference. Evidence (E1) states that the existing interferences have been identified and classified. This has been achieved because an expert, who masters the architecture, has reviewed and double-checked two activities (strategy (W2)). Evidence (E4) points to a report that summarizes which interferences have been identified, how they have been identified, and why the identification is sound and complete. Evidence (E5) points to a safety report that details the effects of each interference on the hosted applications. Those effects can be expressed in different units (e.g. delay, bandwidth). If expressed in delays, the questions are
what will be the impact of interference on the WCET (Worst Case Execution Time) and/or on the WCRT (Worst Case Response Time) of each application?
and are these slow downs acceptable?
From this information, the applicant has defined dequate means of mitigation to prevent, for instance, unacceptable effects. Evidence (E3) collects all those means of mitigation, how they mitigate each unacceptable interference and how they were verified.